projects:cybersecurity:journalclub
2023 Journal club
---- ===== DATETIME ===== ^ Title | | ^ Authors | | ^ Journal | | ^ URL | | ^ Summary | | Comments: * Questions: *
2023-02-13 Friday
| Title | DecIED: Scalable 𝑘-Anonymous Deception for IEC61850-Compliant Smart Grid Systems |
|---|---|
| Authors | Dianshi Yang, Daisuke Mashima, Wei Lin, Jianying Zhou |
| Journal | CPSS '20, October 6, 2020, Taipei, Taiwan |
Context: Part of CS5321 Network Security module, whose lecturer is author (Mashima).
Novelty: Implemented a deception network for smart grid systems compliant with a substation standard IEC61850.
Mechanism:
- High interactivity decoy network
- Logging of real device messages emitted on the network, then having devices replicate messages
- Unique AppIDs are assigned and set to be ignored by real devices
Takeaways:
- Attackers, after successful penetration of smart grid system, typically hide in the system for several months to actively interact with devices, or stay completely passive to sniff network messages to derive network topology.
| Title | CAUDIT: Continuous Auditing of SSH Servers To Mitigate Brute-Force Attacks |
|---|---|
| Authors | Phuong M. Cao, Yuming Wu, and Subho S. Banerjee, UIUC; Justin Azoff and Alex Withers, NCSA; Zbigniew T. Kalbarczyk and Ravishankar K. Iyer, UIUC |
| Journal | 16th USENIX Symposium on Networked Systems Design and Implementation (NSDI ’19) |
Novelty: Farming of SSH attacks on an /16 address space (65k hosts) within NCSA peer-to-peer global cluster, which are then used for auditing of production network which may host improperly secured SSH hosts.
Mechanism:
- Use of non-interactive honeypots for scalability to millions of honeypot intrusion attempts
- Continuous audits performed on production network by replaying attack attempts recorded by honeypot
- Use of black hole router (BHR) to block SSH attempts at network border
Threat model: Assume attackers perform SSH-credential guessing attacks, and are not aware of the honeypot address space.
Takeaways:
- SSH attacks are performed via compromised router/IoT devices (
sshlib 0.1), CVE-2018-10933 auth bypass (libssh2 1.7.0), or fake SSH clients (PuTTy)
- The BHR is used to funnel blacklisted IPs that make a single login attempt to honeypot, by dropping irrelevant packets using a flow-shunting tool before they even reach the kernel networking stack. Flow shunting implemented with eXpress Data Path (XDP) to identify SSL/TLS handshake
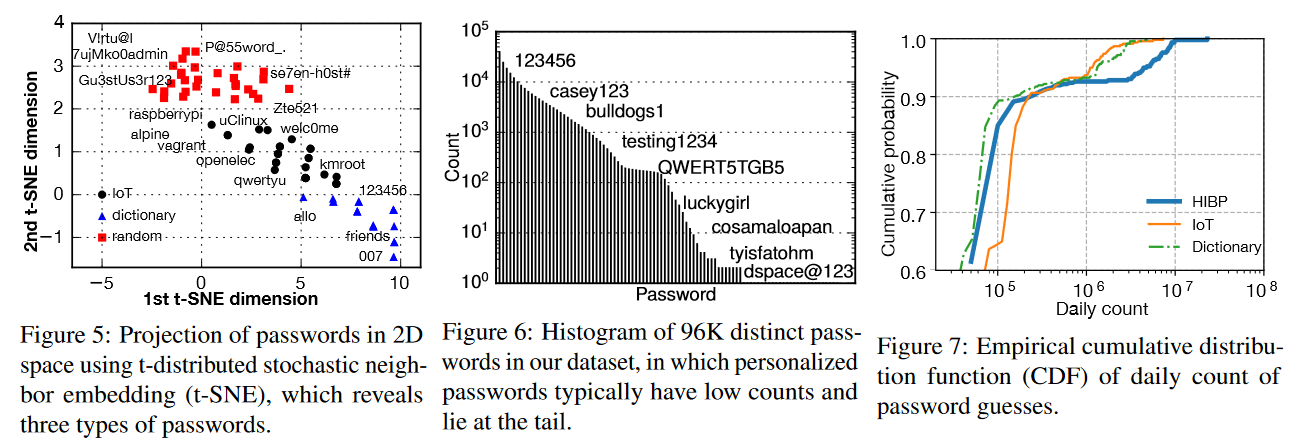
- Distribution of attack password space can be grouped into three clusters: (1) HaveIBeenPwned database, (2) typical IoT password attacks, (3) dictionary attacks
projects/cybersecurity/journalclub.txt · Last modified: 3 years ago ( 2 May 2023) by 127.0.0.1